← use case diagram of cyber security cyber security system architecture diagram →
If you are searching about Cybersecurity diagram you've visit to the right page. We have 20 Pics about Cybersecurity diagram like Diagram A | PDF | Cybercrime | Computer Security, Cyber Security Diagram – NBKomputer and also Diagram of Cybersecurity Stock Photo - Alamy. Here it is:
Cybersecurity Diagram
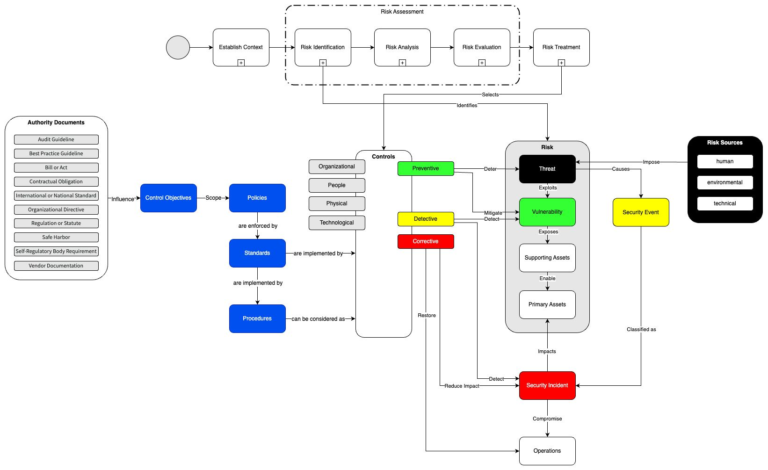 joapen.com
joapen.com
Diagram Of Cybersecurity Stock Image. Image Of Contractors - 117562251
 www.dreamstime.com
www.dreamstime.com
cybersecurity
Diagram A | PDF | Cybercrime | Computer Security
 www.scribd.com
www.scribd.com
Cyber Security Incident Response Process Flow Chart Ppt, 55% OFF
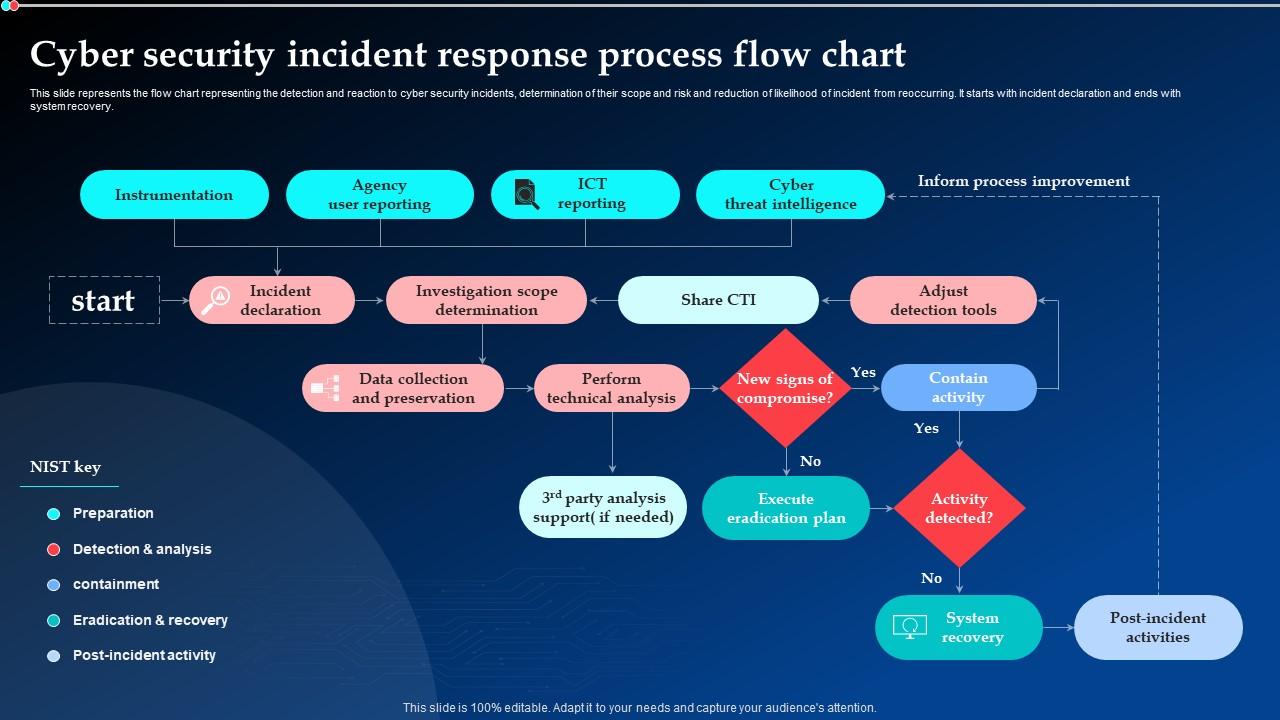 gbu-taganskij.ru
gbu-taganskij.ru
A Human-Centered Cybersecurity Approach | Mindflow
 mindflow.io
mindflow.io
Cyber Security Diagram – NBKomputer
 nbkomputer.com
nbkomputer.com
Diagram Of Cybersecurity Stock Photo - Alamy
 www.alamy.com
www.alamy.com
Diagram Of Cybersecurity Stock Photo - Alamy
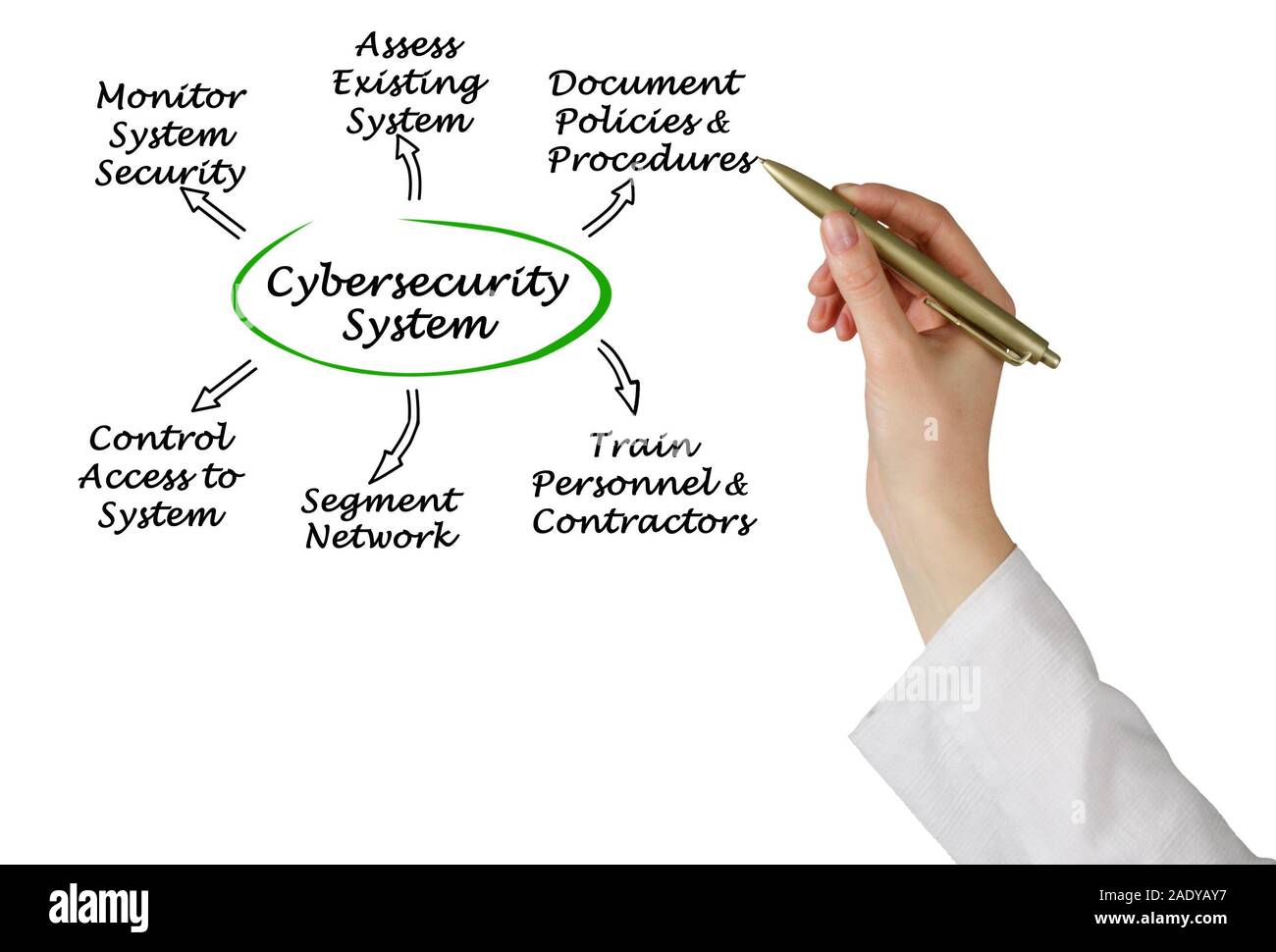 www.alamy.com
www.alamy.com
Cybersecurity Component Architecture. | Download Scientific Diagram
Diagram Of Cybersecurity Stock Photo - Alamy
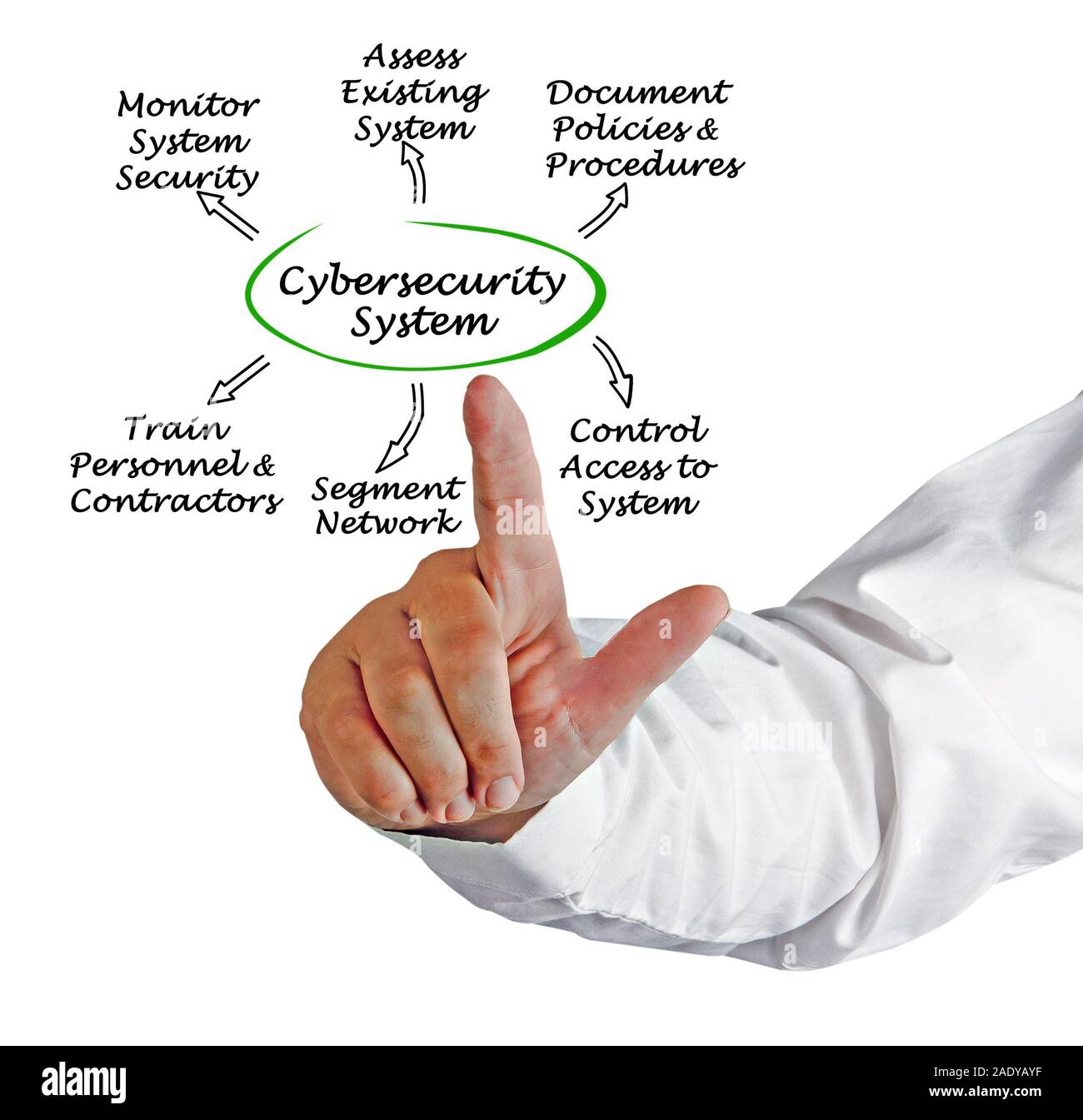 www.alamy.com
www.alamy.com
Cyber-security, Cyber Crime
 ilearncana.com
ilearncana.com
Diagram Of Cybersecurity Stock Photo - Alamy
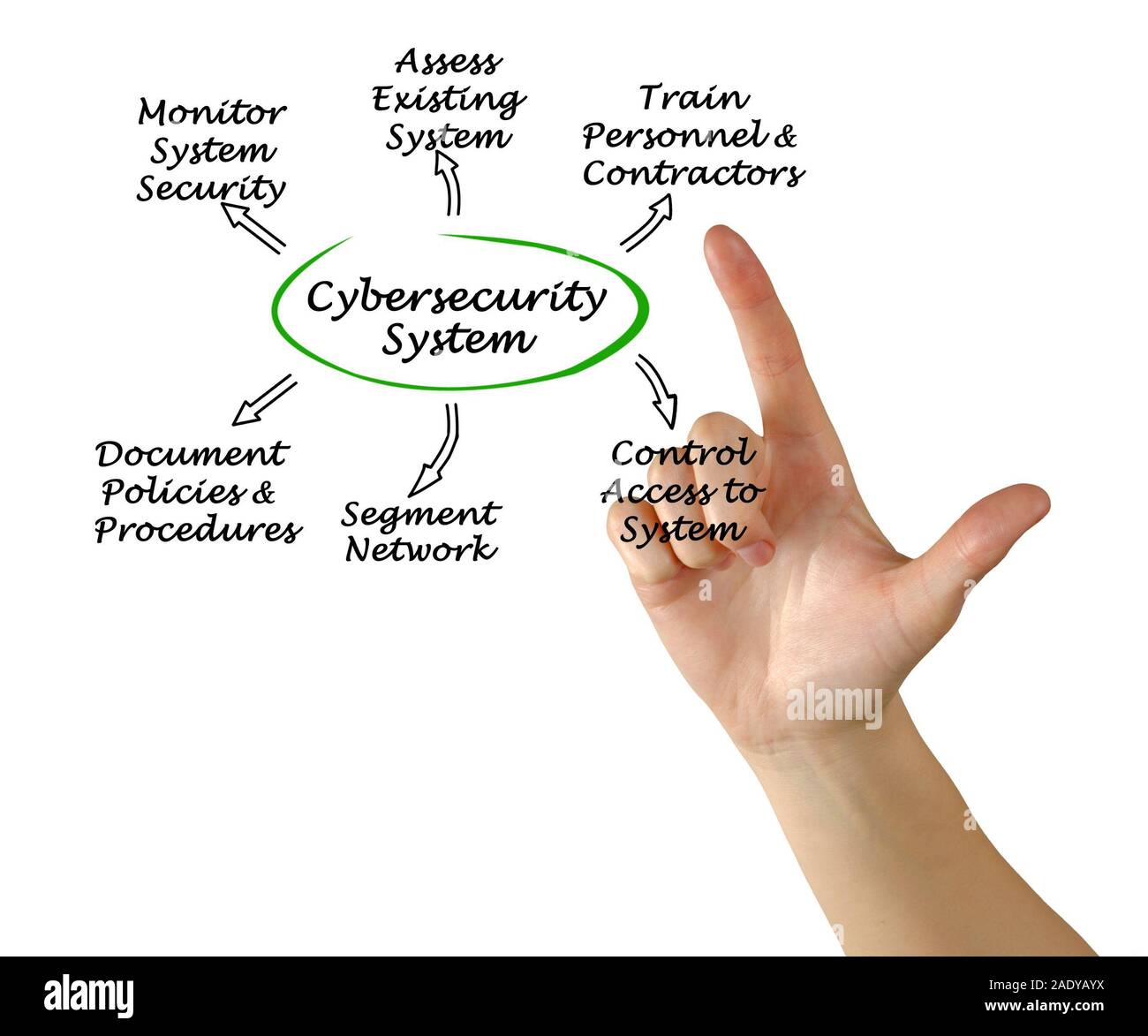 www.alamy.com
www.alamy.com
A Human-Centered Cybersecurity Approach | Mindflow
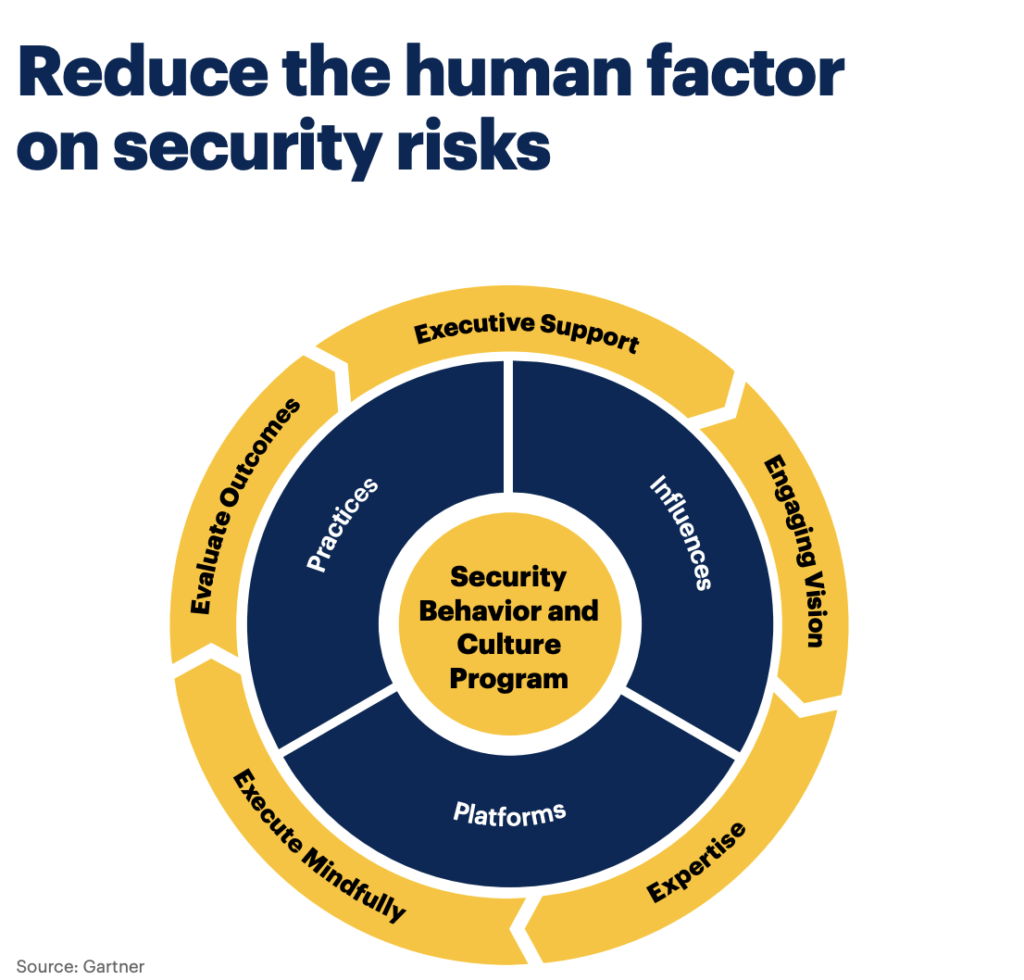 mindflow.io
mindflow.io
Law Enforcement, Privacy And Security In Dealing With Cybercrime
 www.studocu.com
www.studocu.com
Cyber Security Graph
 mungfali.com
mungfali.com
Cybersecurity Architecture & Roadmap | Managed Sentinel
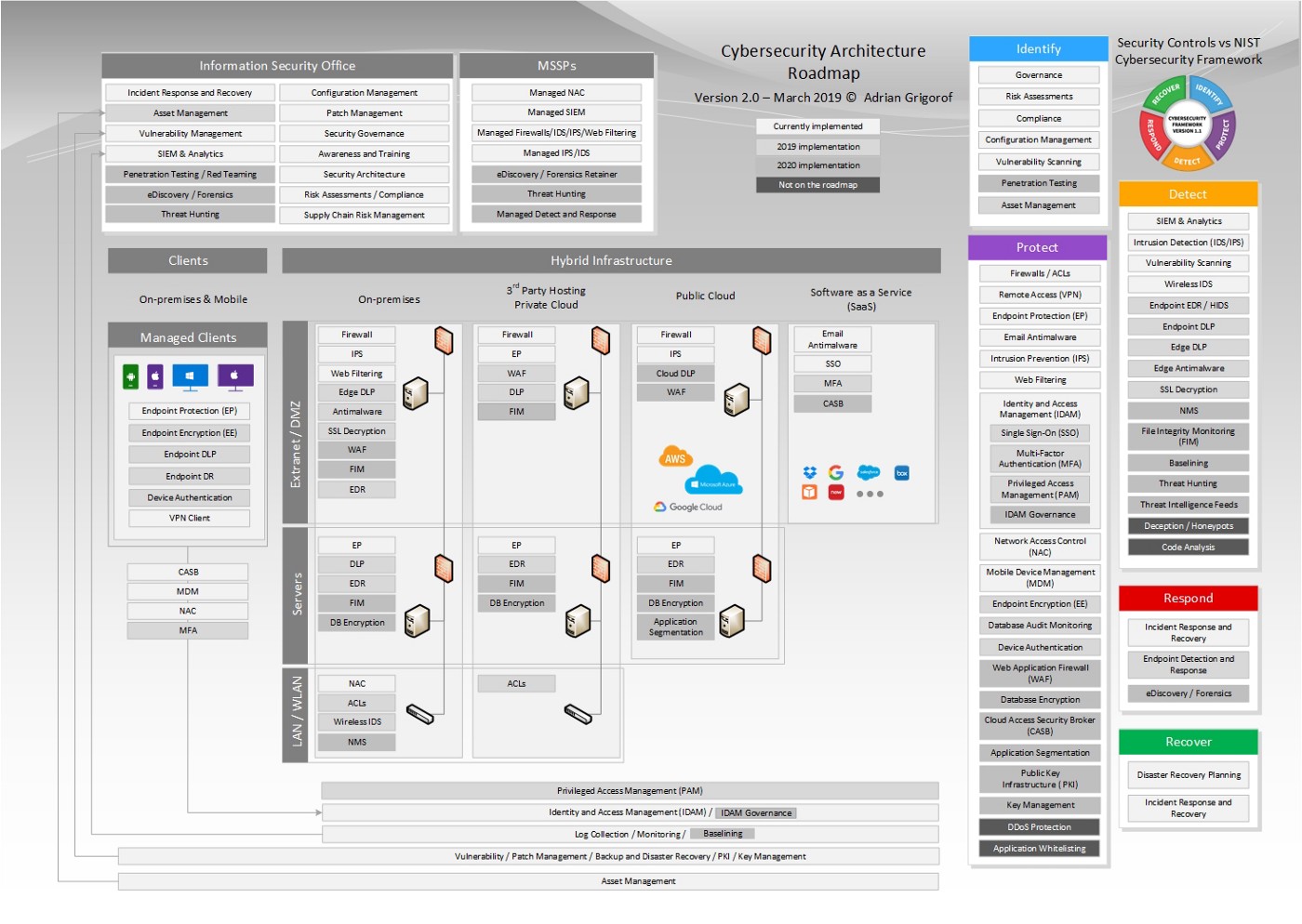 www.managedsentinel.com
www.managedsentinel.com
architecture cybersecurity roadmap diagram visio future current sentinel executive one
Cybersecurity Risk Management Framework Multitiered Risk Management
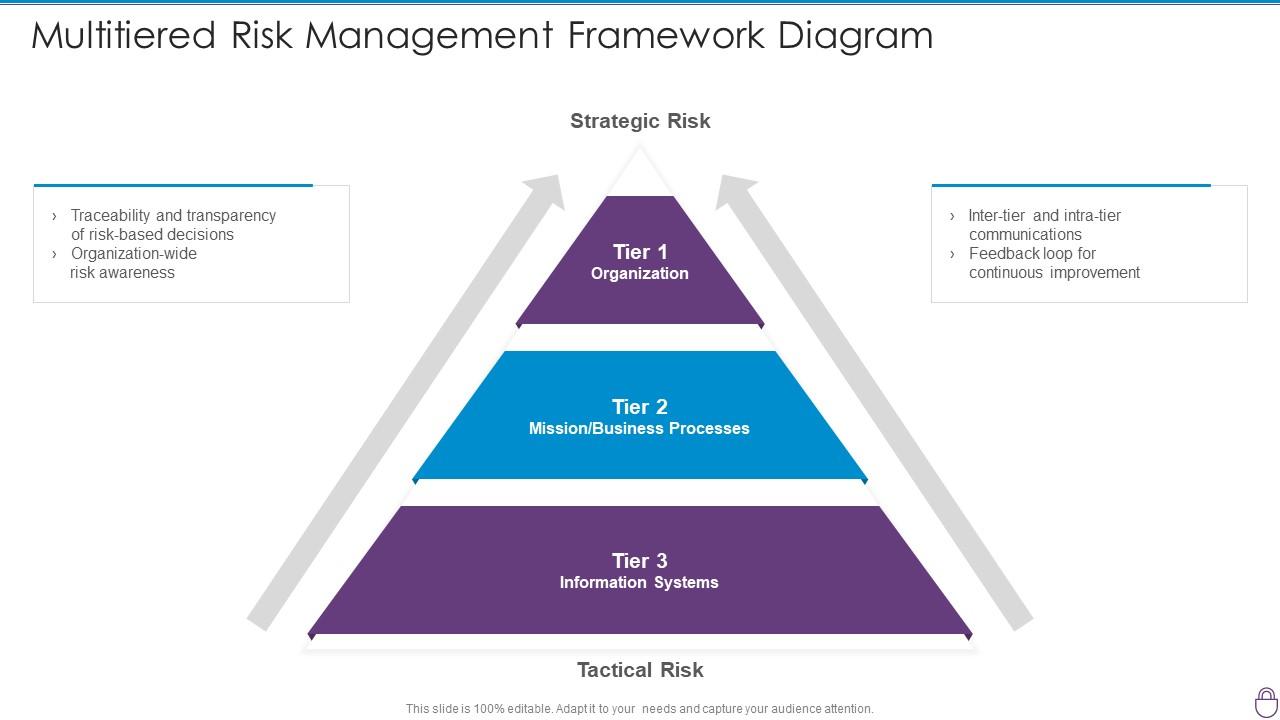 www.slideteam.net
www.slideteam.net
Law Enforcement Blue Gradient Concept Icon. Public Security. Police
Types Of Cyber Security [17] | Download Scientific Diagram
![Types of cyber security [17] | Download Scientific Diagram](https://www.researchgate.net/publication/371559986/figure/fig3/AS:11431281167801403@1686762144946/Types-of-cyber-security-17.jpg) www.researchgate.net
www.researchgate.net
A Human-Centered Cybersecurity Approach | Mindflow
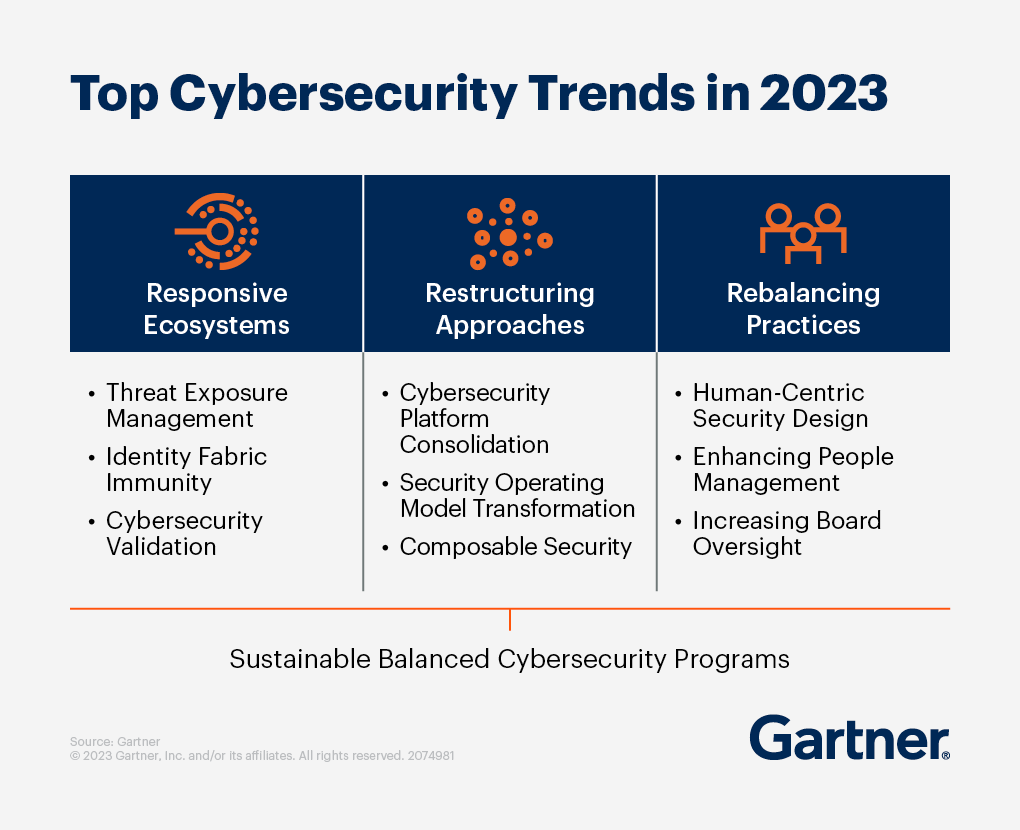 mindflow.io
mindflow.io
Diagram of cybersecurity stock photo. Law enforcement, privacy and security in dealing with cybercrime. A human-centered cybersecurity approach