← cyber security system architecture diagram visual diagram of cyber security →
If you are looking for Building an Advanced Cybersecurity Plan: Access Control you've visit to the right place. We have 20 Pics about Building an Advanced Cybersecurity Plan: Access Control like Diagram A | PDF | Cybercrime | Computer Security, Cyber Security Diagram – NBKomputer and also 3: The Component-based Access Control security pattern: sequence. Here it is:
Building An Advanced Cybersecurity Plan: Access Control
 mfgtech.org
mfgtech.org
Cybersecurity Diagram
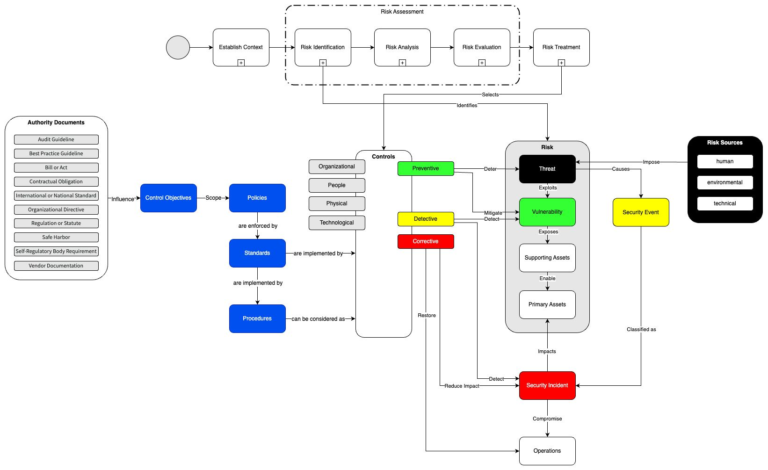 joapen.com
joapen.com
Access Control Security System - Security Guards Companies
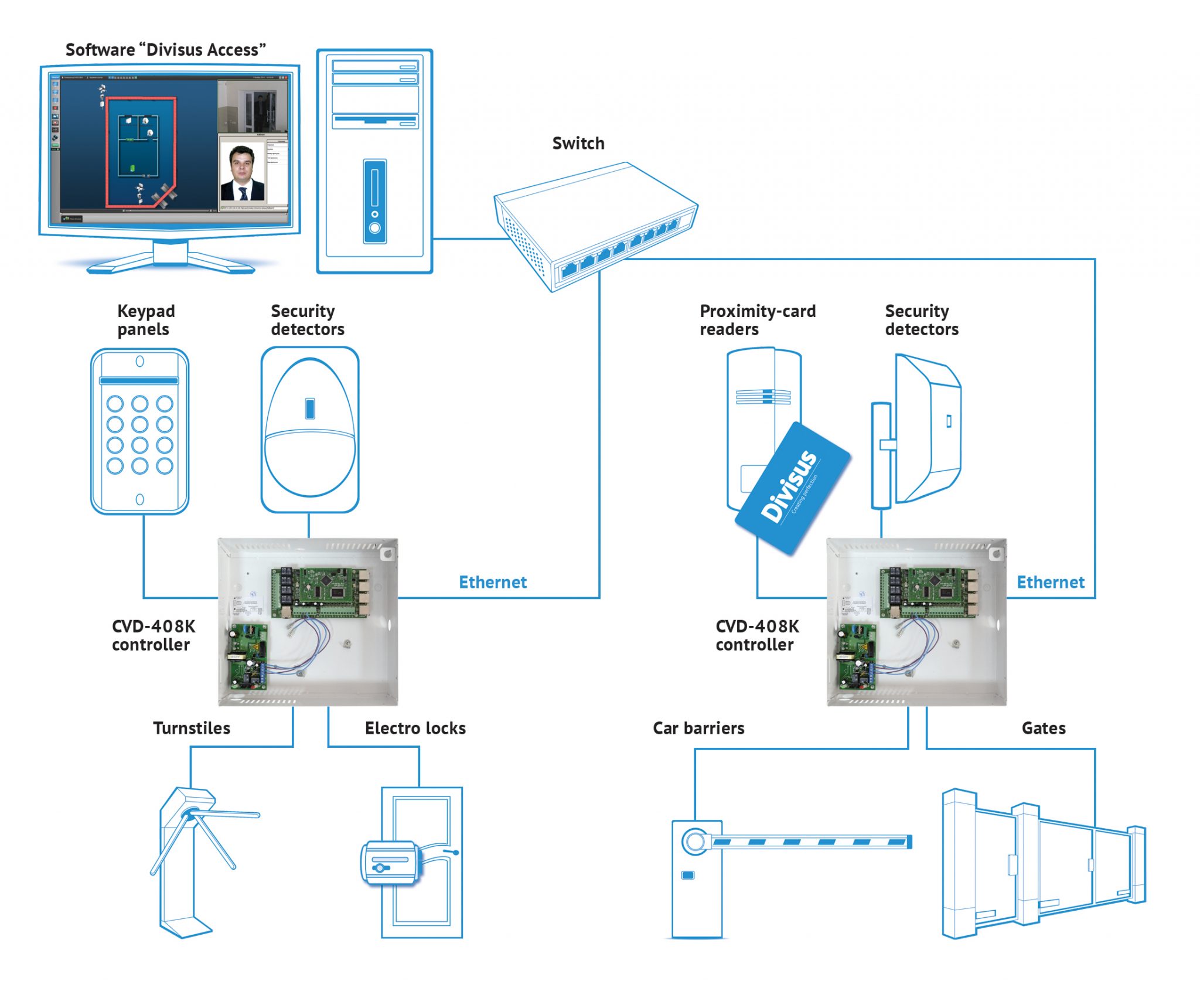 www.security-guard.ca
www.security-guard.ca
fog
Diagram Of Cybersecurity Stock Photo - Alamy
 www.alamy.com
www.alamy.com
Access Control System Schematic Diagram
 www.circuitdiagram.co
www.circuitdiagram.co
Access Control Design Tips Part #5 (Cybersecurity) - EvTrack Visitor
 evtrack.com
evtrack.com
cybersecurity security firewall routers appropriate
Cyber Security Secure Network Diagram Building Controls Systems - KW
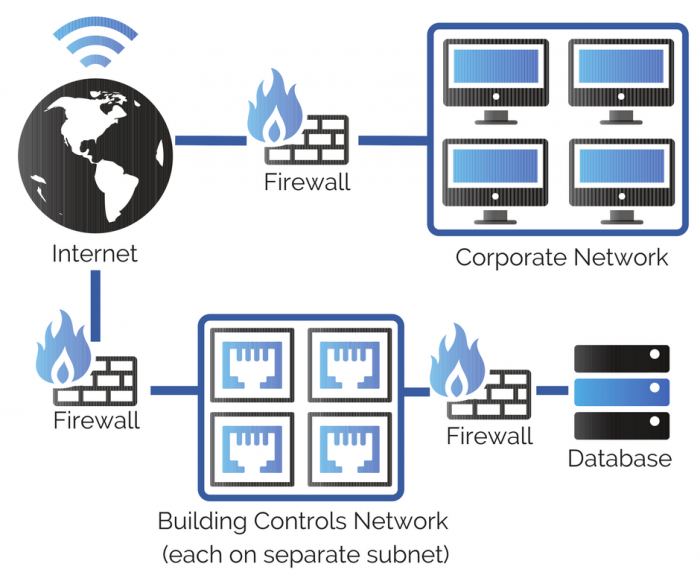 www.kw-engineering.com
www.kw-engineering.com
cyber cybersecurity
Diagram Of Cybersecurity Stock Photo - Alamy
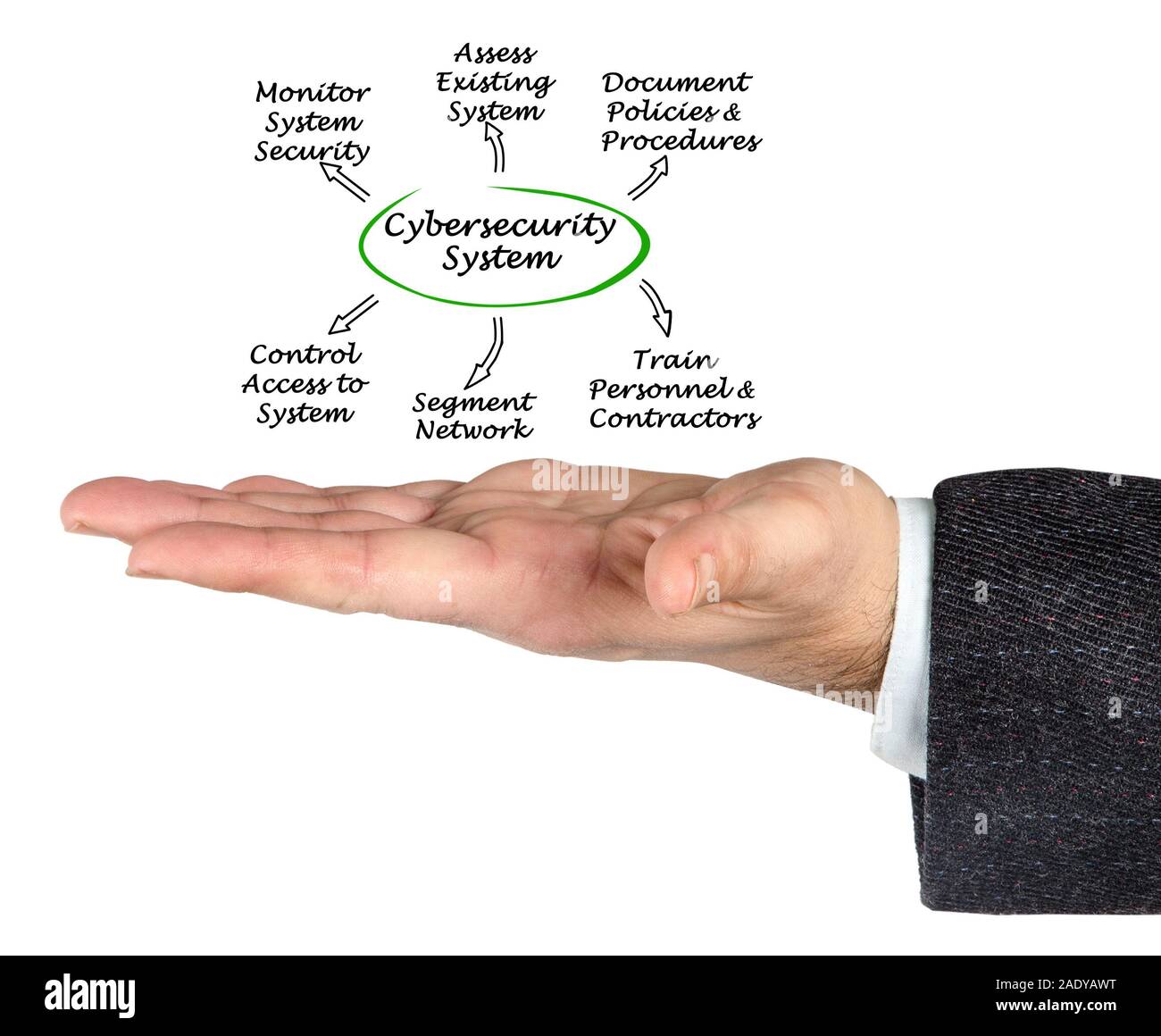 www.alamy.com
www.alamy.com
Cybersecurity Overview – Part 2: Cybersecurity Authorization And Access
 networkbuilders.intel.com
networkbuilders.intel.com
Access Control Cyber Security Concept Secure Stock Illustration
 www.shutterstock.com
www.shutterstock.com
Diagram Of Cybersecurity Stock Image. Image Of Control - 97280825
 www.dreamstime.com
www.dreamstime.com
cybersecurity diagram preview
Access Control Block Diagram. | Download Scientific Diagram
 www.researchgate.net
www.researchgate.net
Cyber Security Diagram – NBKomputer
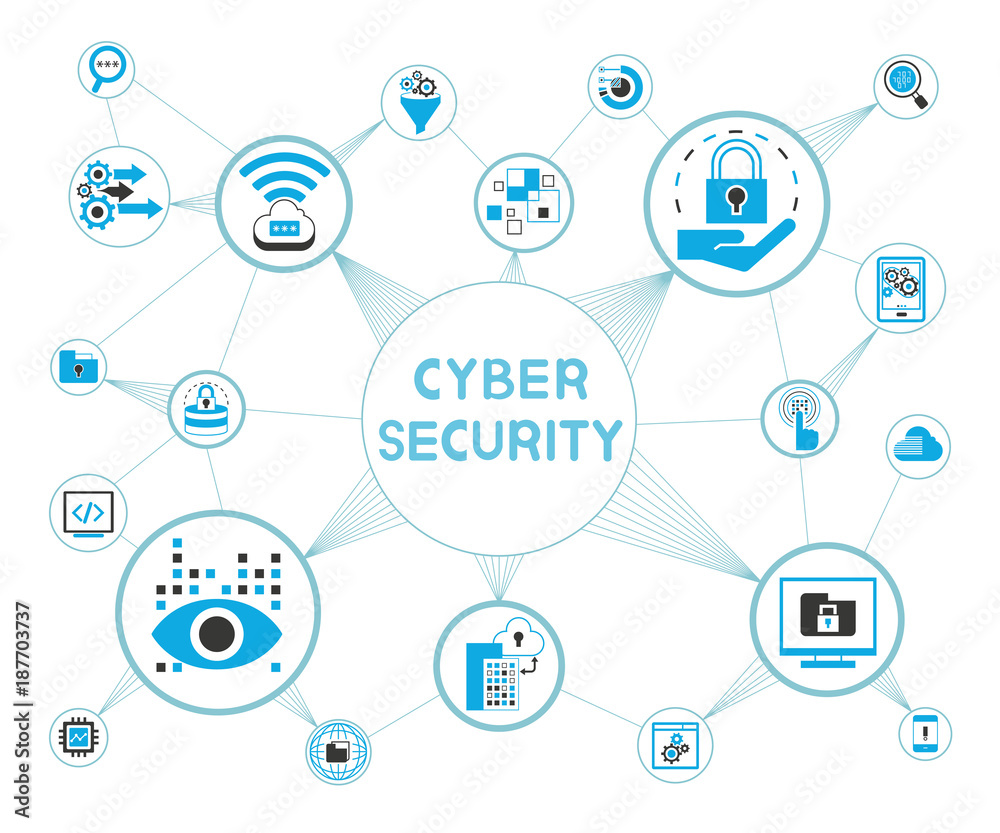 nbkomputer.com
nbkomputer.com
Diagram Of Cyber Security Stock Photo By ©vaeenma 154364596
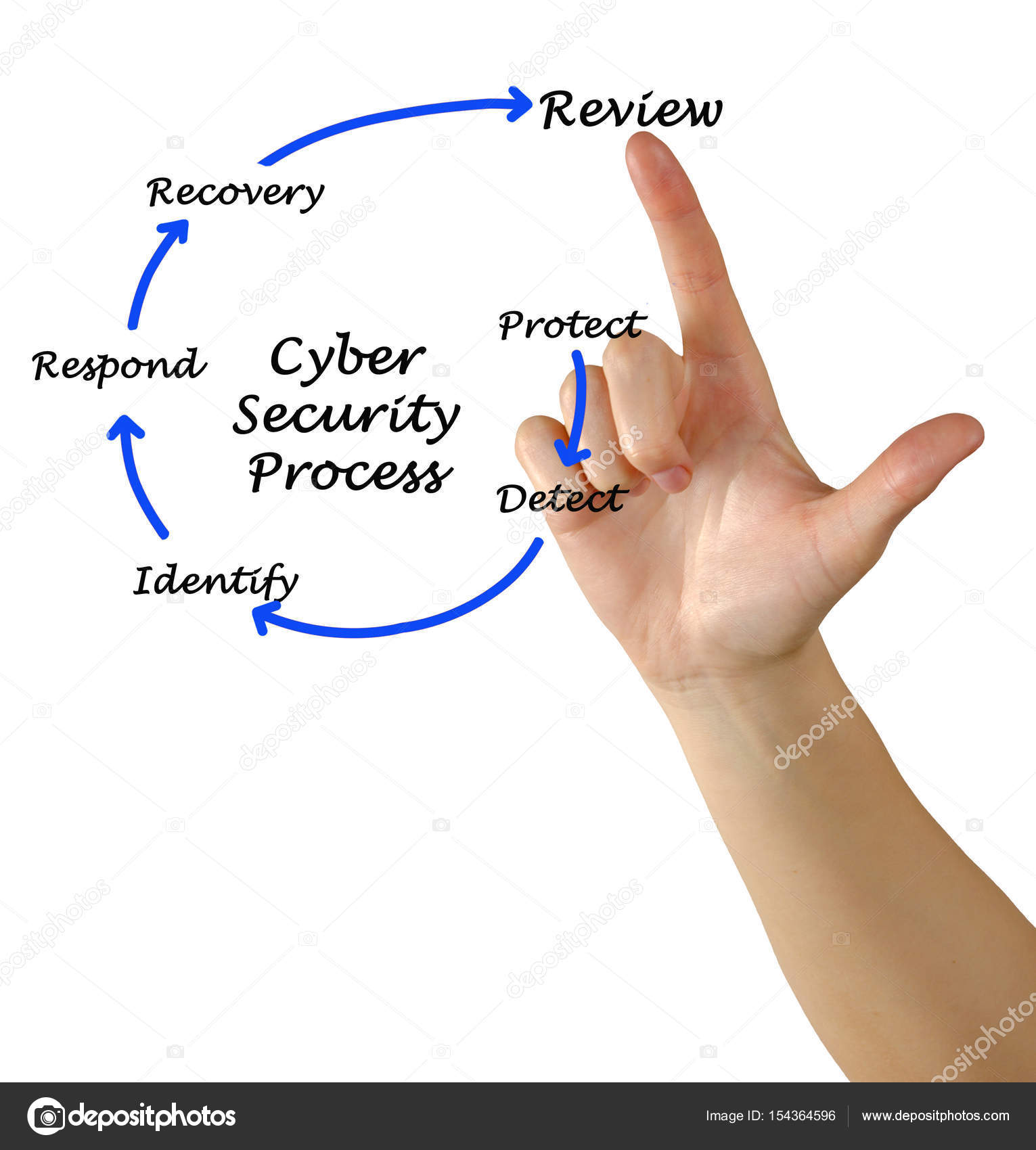 depositphotos.com
depositphotos.com
Access Control And Cyber Security Concept Stock Illustration
 www.dreamstime.com
www.dreamstime.com
ACLs In Cybersecurity: Managing Access Control Effectively - Blue Goat
 bluegoatcyber.com
bluegoatcyber.com
Premium Photo | D Illustration Of Access Control In Cyber Security And
 www.freepik.com
www.freepik.com
Cyber Security Diagram
 mavink.com
mavink.com
3: The Component-based Access Control Security Pattern: Sequence
 www.researchgate.net
www.researchgate.net
Diagram A | PDF | Cybercrime | Computer Security
 www.scribd.com
www.scribd.com
3: the component-based access control security pattern: sequence. Acls in cybersecurity: managing access control effectively. Diagram of cybersecurity stock image. image of control